It’s no surprise that the return to the office has forced many organizations to accelerate their safety, security and compliance technology modernization programs. The need to keep workplaces safe from COVID-19 outbreaks has prompted the rapid implementation of touchless visitor management technology, health screening questionnaires and contact tracing solutions.
Now as many companies reopen with a greater focus on safety and security, they are actively evaluating upgrades to their core workforce access and visitor management platforms.
While the business issues that underpin the justification for a Visitor Management System upgrade will be unique to every organization, this post is designed to help companies deliver an investable business case for an Enterprise Visitor Management System.
1. THE CASE FOR A VISITOR MANAGEMENT SYSTEM UPGRADE
Typically, an existing Visitor Management solution was purchased as a replacement for a paper visitor logbook which had failed to meet the requirements of the standards and regulations at the time. As organizations grow, the volume of visitors, contractors, vendors and non-nationals increases, and that replacement for the paper logbook will again struggle to meet complex safety, security and compliance requirements.
Continued Visitor Management compliance failures will become an ongoing audit issue, which in turn jeopardises certification and the commercial arrangements linked to it.
The upgrade to an Enterprise Visitor Management system also delivers additional opportunities:
- Physical identity management — Integration with the physical access control system creates a central source of physical identities and profile attributes for every employee, visitor, contractor and vendor with access to facilities
- Access management – Manage access rights to facilities based on policy, regulations, safety requirements, purchase requests and many more attributes, from onboarding, updates and removals
- Badge management – Manage credentials or badges that deliver physical access to facilities
- Integrations and APIs – Integrate with corporate HR, learning management and ERP systems so physical access rights dynamically align with corporate identity profiles
- Reporting and analytics — Quickly and accurately deliver reporting for physical access governance, risk and compliance activities
- Evacuation management — Creates a consolidated list of every person in every facility, and emergency response can be improved with accurate personnel location data
- Contact tracing — Turn existing building access cards into a digital contact tracing solution to quickly and accurately identify employees, visitors, contractors and vendors who have been exposed to an infected person
2. OBJECTIVES OF AN ENTERPRISE VISITOR MANAGEMENT UPGRADE
Organizations will build specific, measurable objectives based on their own data, and security, risk and compliance reviews. Typically their objectives will fall into categories like the following:
- Service improvement — Projected improvements in Service satisfaction scores will largely drive this objective
- Cost reduction – Measurable reductions in direct and indirect costs will form the basis of this measure
- Improved security – Security Vulnerability Assessments will detect problem areas, and resolution of identified issues will form the basis of this measure
- Improved safety – Many organizations record and collect information on safety incidents, this objective will contribute to reductions in reportable safety incidents
- Improved compliance — Audits will detect problem areas, and resolution of identified issues will form the basis of this measure
- Extensible platform — Identify opportunities to scale the solution as the organization expands and its safety, security and compliance requirements evolve.
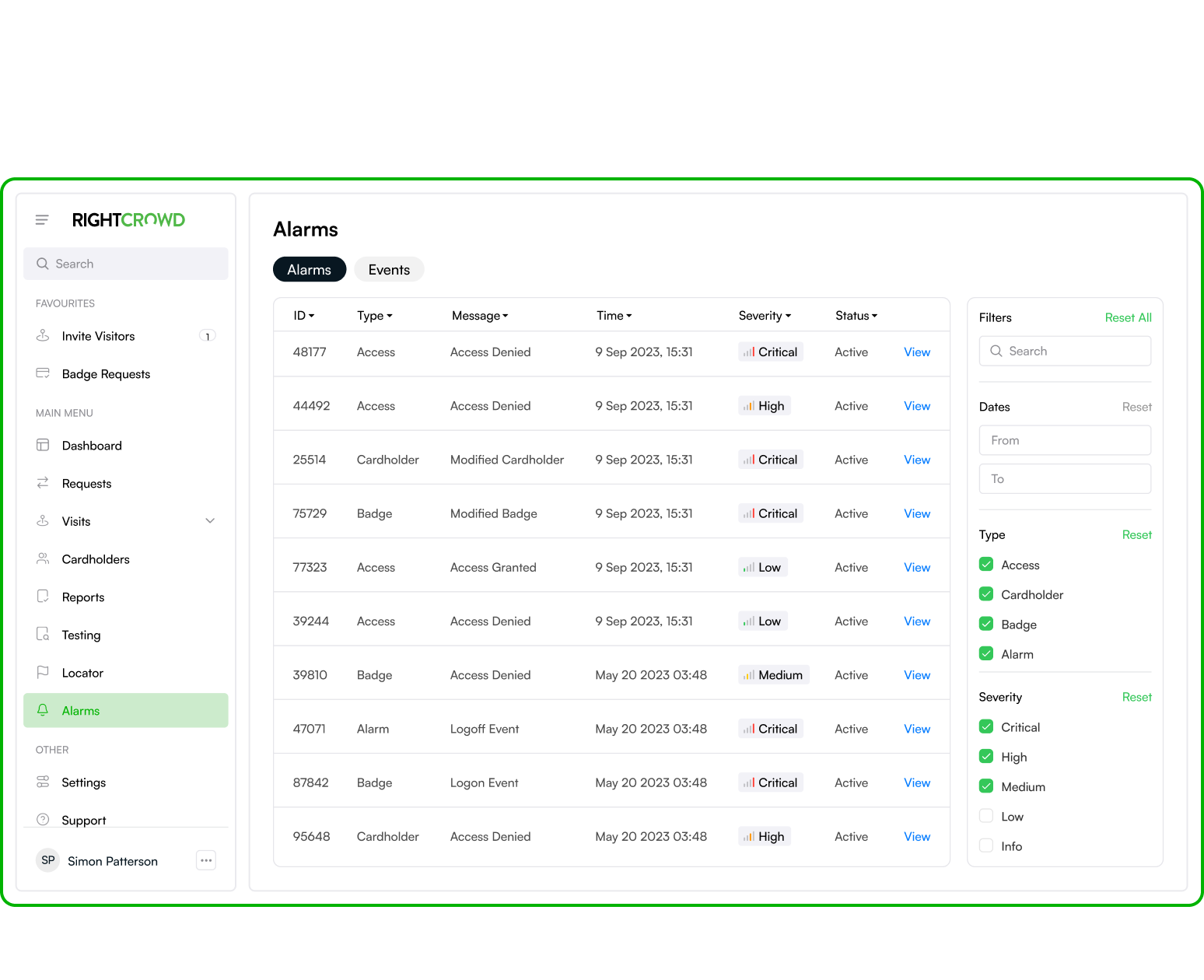
3. BENEFITS OF AN ENTERPRISE VISITOR MANAGEMENT UPGRADE
Enterprise Visitor Management solutions can be used to initiate, approve, record and update visitor, contractor and vendor profiles and their related physical access permissions. This in turn improves productivity, lowers processing cost and improves security and compliance outcomes. The following are some other benefits to consider:
- Improved service delivery – Enterprise solutions include a number of self-service features for hosts and visitors, and automated approval processes that deliver higher service levels than standards solutions and manual processes
- Cost reduction — Process automation improves productivity, reduces the cost per transaction, and vastly improves security and compliance outcomes. Automation can also enable contractors, vendors and non-citizens with appropriate access with higher accuracy, locking in regulatory compliance within every process step
- Improved resource utilization – Automating visitor access management processes allows security departments to operate more efficiently by decreasing the number of people, time and infrastructure that would be required to manage access additions, changes and removals at scale
- Improved safety outcomes – In the context of COVID-19 business leaders need to understand the risks of people contracting the virus in their workplace and taking reasonable steps to prevent the spread. Keeping infected people out of the building through pre-entry health checks and inductions, thermal scanners and contactless technology integrated into the Enterprise Visitor Management system will help to achieve that
- Improved policy compliance — Visitor access privileges are granted according to policy, and all individuals and services are properly authenticated, authorized and auditable.
- Improved security posture – Companies that properly manage identities have greater control of user access, which reduces the risk of security breaches
- Employee self-service — Common physical access management processes can be managed by host and visitors off-site, and kiosks and mobile applications on-site, allowing security operations to focus on critical risks and security management rather than administrative tasks.
- Security risk management — Enterprise solutions better enforce policy compliance around access approvals and privileged access, and address issues regarding privilege creep, insider threat and hybrid working arrangements
- Adaptable physical access delivery — Enterprise Visitor Management solutions provide attribute-based physical access, to ensure visitors, contractors and vendors have the right access every time they enter facilities
- Improved audit outcomes — Enterprise Visitor systems help companies demonstrate that physical access management processes are enforced, with auditable reporting available on demand
4. PROCUREMENT OVERVIEW
Many organizations have mature processes to support vendor selection and purchasing. The vendor selection process outline would include some of the following elements:
- Request for information – Vendor screening and preselection are used to evaluate the solutions and capability of a broader set of suppliers to ensure the RFP is only issued to suitable and qualified organizations
- Request for proposal (RFP) — The RFP seeks a detailed commercial proposal to design and deliver an extensible Visitor Management platform suitable for the organizations’ operating environment, functional requirements and objectives.
- Proposal evaluation — Bid evaluation criteria are developed in line with the project objectives, functional requirements and commercial offer. Proposals are then evaluated in line with the criteria and moderated by purchasing.
- Proof of concept (POC) — This step is used to evaluate the vendor’s solution and delivery capability in a live environment based on a set of defined scenarios. This step may still include a number of competing vendors.
- Vendor selection — Based on the results of the evaluation of the RFP and POC, commercial offer, and business feedback the final vendor selection is made. A project-specific evaluation sheet is delivered as part of the business case.
5. SOLUTION, DELIVERY AND COST SUMMARY
This section provides an overview of the preferred vendor’s solution, and how the system delivers on the key requirements.
The project delivery approach would also be outlined, followed by a project investment cost and cash flow summary.
6. RISKS ASSESSMENT
A risk assessment is undertaken to identify existing and potential risks (and residual risks) in terms of consequences and likelihood. The RA can be developed qualitatively or quantitatively. is usually conducted using the organization’s established evaluation process to identify and rank, and to prioritise those resulting risks.
As risks are defined and mitigation measures developed, cost-benefit decisions about the remaining or residual risk are made. Risks can be eliminated, reduced, transferred (often by insurance of contracts to third parties) or accepted. A highly skilled team of security risk practitioners will usually lead and coordinate the process, in a consultative manner.
A risk matrix would be delivered as part of the business case.
| Capability | |||||
| Risk | Prevent | Detect | Respond | Recover | Impact |
| 1 | Low | Low | Moderate | Low | $ |
| 2 | Moderate | Moderate | Low | Low | $ |
| 3 | Moderate | Low | Moderate | Low | $ |
| 4 | High | Modersate | Low | Low | $ |
7. RECOMMENDATION
Typically a number of candidate options and a recommendation would be presented at this stage. These might include:
1. Upgrade Visitor Management System
This is the best option to address the risks associated with requirements for Visitor Management across the organization.
2. Defer project:
Defer the Visitor Management System upgrade and do not proceed within the timeframe of the next regulatory window.
However, due to the current commercial arrangement relying on continued certification, and the current risks of the existing solution, this is not considered to be a prudent solution as it may expose the company to:
- Cancellation of contracts
- Unacceptable security risks
- A reduction in the ability to deploy future applications
- A reduction in the availability of services
- A reduction in the integrity of services An inability to comply with regulatory obligations or requirements.
For many organizations developing an investable business case for safety, security and compliance technology upgrades was difficult in the past. COVID-19 has changed the landscape and is accelerating technology modernization projects to help companies deal with the operational, legal and regulatory risks a workplace outbreak presents.
To find out more about RightCrowd Enterprise Visitor Management please contact us.